This month is the 100th anniversary of Alan Turing’s birth. There will be world-wide celebrations to acknowledge Alan Turing’s tremendous contributions to Computer Science as well as his contributions to the outcome of World War II through his code breaking efforts. Here is my video of the visit to Bletchley Park to look at how Alan Turing worked together with his brilliant colleagues brought together at Bletchley Park:
For my Computing Conversations column for the June 2012 issue of IEEE Computer magazine we wanted to be part of the celebration. I wanted to examine Alan Turing’s time at Bletchley Park from the point of view of a multi-disciplinary research effort to solve the most pressing issues in cryptography during World War II. I had the following graphic drawn by Matt Pinter to use in the video and in the article. 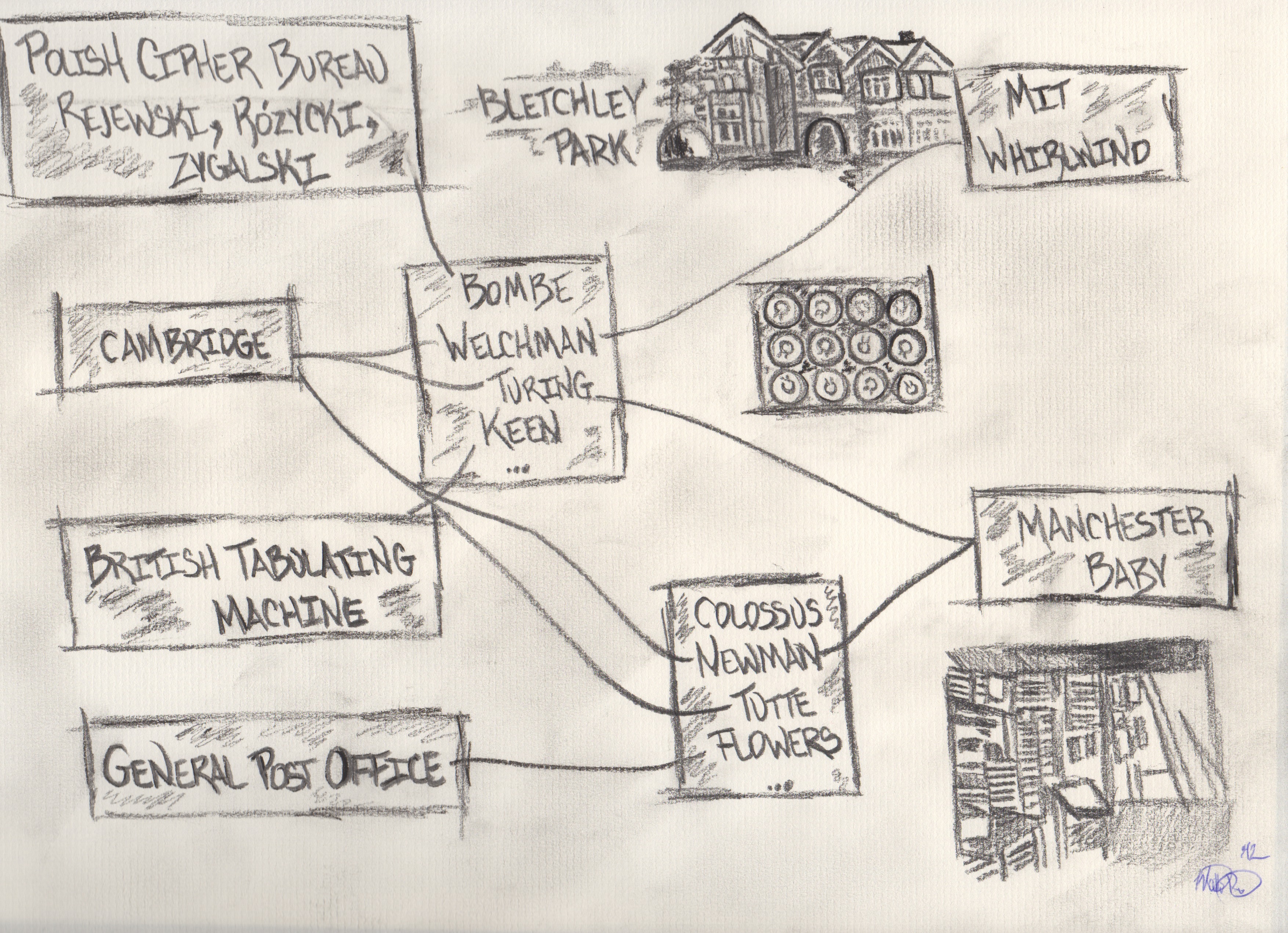 The theme of the image is a play on the “six-degrees of Alan Turing” and focused on the embeddedness of his work at Bletchley Park as well as focus on the evolution of mechanical computing into electronic computing during World War II.
The theme of the image is a play on the “six-degrees of Alan Turing” and focused on the embeddedness of his work at Bletchley Park as well as focus on the evolution of mechanical computing into electronic computing during World War II.
In the quest to break the codes of their opponents in World War II, the people at Bletchley Park pushed the frontier of computation forward at a high rate of speed. World War II was the first war that operated at a scale and speed that required communication to be done using wireless transmissions. Since wireless communication can be monitored by ally and enemy alike, it is necessary to encrypt transmissions. In order to communicate securely at scale, it was necessary to develop mechanical encryption and decryption machines in order to produce an “un-crackable” encipher system.
Just like in modern encryption, it was (and continues to be) impossible to hide the technical details of how encryption and decryption was/is done. Given that the encryption technique would be revealed or reverse-engineered sooner or later, the only defense was to make it computationally “impossible” to determine the key and then change the key regularly enough that it was/is simply impractical to try to crack the encryption and determine the key. The goal was to make it so computationally painful than no one would even attempt to break the code.
The winning side in this computational war would be the one who could compute quickly enough to decrypt transmissions so that the information would still be useful. If for example, the enemy sends 1,000 messages per day and changes the key every day, and it takes two months to decrypt a single message, by the time a message was finally decrypted it would have little or no value from a military perspective. And if you chose the wrong message to decrypt, the information would be completely useless.
If you could get to the point where you could quickly decrypt a large fraction of the messages in a timely manner you could correlate across all the messages for a given day as well as across a series of messages on a topic over time. Such intelligence would be (and was) extremely valuable in pursuing a war to a successful conclusion and minimizing loss of life.
Project “Ultra” was that overarching effort to decrypt massive numbers of messages and then produce low-level and high-level intelligence provided to Winston Churchill and his top generals.
Another key was to keep the enemy believing that their encryption was unbreakable so that they would confidently continue to use their encryption and not develop new encryption techniques. The key to making it all work was to build computing machines that were so much faster than the enemy could imagine.
As the war started, with the help and inspirations of Polish cryptographers who had successfully developed a system to decipher German enigma traffic, Alan Turing developed an electro-mechanical system called the BOMBE that electronically tested possible key values so quickly that it made breaking German traffic encrypted with the Enigma (and similar) machines a tractable problem and ultimately a routine activity. While Turing designed the core algorithm for the BOMBE, it was engineered and built by Harold (Doc) Keen, and optimized with the addition of the “Diagonal Board” by Gordon Welchman. They key was that while Turing played a central role in the making of the BOMBE – his creativity was amplified by the contributions of hundreds of other people.
The other computing machine featured in the video is the Colossus that has been reconstructed and runs in the National Museum of Computing at Bletchley Park. While Turing is credited with developing the decryption technique for the more advanced Lorenz SZ42 encryption machines used by Hitler for longer strategic computations, other created the necessary solutions and systems to enable the regular decryption of these high-command messages. Bill Tutte worked out the details of how the Lorenz machine was built and enabled the construction of a “clone” machine. Tommy Flowers devised and constructed a tube/valve-based computer to automate the process of figuring out the key sequence for a particular message. Max Newman ran the production facility and created the processes and structure to enable the breaking of the codes. Again very much a team effort with Turing as making a contribution amplified by the talents of others.
All in all my favourite aspect of the video is the juxtaposition of the BOMBE and the Colossus.
The BOMBE represents as far as we could advance mechanical computation. It was cleverly designed, cleverly optimized, and made to be as fast as it possibly could go. The mechanical bits are lubricated by a fine mist of oil that falls out the bottom of that machine and is collected in a pan. It is an ultimate expression of what one can do moving information through cogs, springs, wheels, contacts, resistors, relays, wire, and light bulbs. It is built to withstand the wear and tear of 24 hour per day seven day per week production use and remain reliable.
And yet with all of the sophisticated engineering of the BOMBE, mechanical computing was no match for the Lorenz SZ42 encryption. The Enigma had three to five encryption wheels and a plug board and the Lorenz SZ42 had 12 encryption wheels. The Lorenz was not practical to break in a reasonable time with mechanical computation. And so the brilliant minds at Bletchley Park had no choice but to invent large-scale high-speed electronic computation to break the Lorenz cipher. They knew the Lorenz machine could be broken. All it would take was faster computation. So the brilliant minds at Bletchley Park threw themselves at the problem until they solved it.
And so in the pastoral setting of the Bletchley Park mansion and outbuildings we see the mechanical computing era give way to the electronic computing era. While all of the electronic computing technology was a closely held military secret that was protected for many years, the world would never go back. The electronic computing age had begun even though it was another 10 years before the rest of the world had much of an inkling of the profound change.
It is why I think it is fair to mark Bletchley Park as “ground zero” for the electronic computing age. Of course there were lots of experiments with electo-mechanical and electronic computational circuits in research labs at universities that pre-date the Colossus, the Colossus is clearly the first electronic computing device that ran at scale and in production 24 hours per day seven days per week.
After the war, people like Turing, Welchman, Newman and others fanned out and created the fledgling field of Computer Science in Britain, the United States and around the world. Computers like the MIT Whirlwind, Harvard Mark I, Manchester Baby, Manchester Mark I, and Ferranti Sirius were general purpose tube-based computers that built on the technology breakthroughs produced at Bletchley Park. All these early break-through electronic computers can trace a bit of their DNA back to the brilliant group of people at Bletchley Park during World War II.
As a note, the Ferranti Sirius was featured in my March 2012 Computing Conversations column where I visited Monash Museum of Computing History in Melbourne, Australia:
If you are interested, here is a podcast of me reading the text of the written column that appears in the June 2012 issue of IEEE Computer magazine:
I hope people enjoy viewing this month’s column video as much as I enjoyed making it. The video was greatly helped by Joel Greenberg. I met Joel many years ago while I was working on Sakai and Joel was working at the Open University in Milton Keynes. When Joel retired from the Open University, he became a volunteer at Bletchley Park. Joel was able to help me get amazing access to the people and facilities at Bletchley Park. We filmed a portion of the video sitting in Alan Turing’s office in Hut 8 at Bletchley Park. The video was filmed May 4, 2012.
There are many people to thank in the making of the Bletchley Park video: the Bletchley Park Trust, the National Museum of Computing, Joel Greenberg, Paul Kellar, Kevin Murrell, Stephen Fleming, and others. I also greatly appreciate the insightful comments from the reviewers of early versions of the video and article.